
Recently, I attended HexaCon 2025 with my coworker @c0w5un.
The holiday called Chuseok began in South Korea before HexaCon, so I was able to take a short trip to Paris before the conference started.
I’m going to write a short review of the trip and HexaCon 2025.
Travel To Paris ✈️
When I left Korea, I was actually quite worried. Because I heard on the news that there are currently protests and general strikes taking place across France. And My colleague visited Germany first and arrived when the HexaCon schedule started, so i’m traveled almost alone!
But the Paris I saw while traveling was peaceful.
Also, I have never experienced pickpocketing during my trip.
There is a time difference of about 7 hours with France, but since my flight from Korea was at 8:30 in the morning, I stayed up all night at the airport so had no trouble adjusting to the time difference. 😂
The architecture, food and atmosphere of Paris were wonderful.👍
I’ve traveled to Rome, Romania, and the United States, but Paris is by far the best.

It was so nice just walking around the Seine River.

 The
The Eiffel Tower and the Arc de Triomphe, which I really wanted to see when I came to France, were truly magnificent.



Also, the traditional French food I ate during my trip was better than I expected. The escargot dish in particular was really delicious.
The duck confit and beef bourguignon were also perfect for my taste.
HexaCon 2025 🗣️
I have participated in POC conference in Korea, but this was my first time participating in a foreign conference.
First Day
The first day began at 9:00 AM at Palais Brongniart, where we had a short coffee break and then listened to the Ivan Krstić's keynote presentation.
Actually, I was surprised at how neatly the presentation was done. The presentation topic was also interesting, as the presenter held the position of Head of Security Engineering + Architecture (SEAR) at Apple. I was very interested in hearing about Apple’s new hardware + software security mitigation, MIE, the increase in bug bounty amounts, and the new bug bounty system that uses flag submissions, similar to CTF.
Also, while listening to the presentation, I agreed with the statement that information on exploit techniques (such as mitigation bypass) will become more valuable than vulnerability information.
Chrome’s V8 engine is also in the process of introducing hardware sandboxes, which will make these combined software and hardware mitigations increasingly difficult to bypass, and exploit techniques for these powerful hardware mitigations will largely remain hidden from the public(Especially MIE).
The other presentations were also very interesting. It would be too long to write about everything one by one, watch the videos when they’re uploaded to YouTube!
Actually, I met a few Koreans at the conference hall on the first day. POC Crew from South Korea and 3 more Korean peoples. It was great to see Koreans at foreign conferences.
Also, on the first day, a speedrun challenge was held. I participated in the preliminary round, but since I had to use the provided laptop, I couldn’t type in Korean. Even when I used a translator, all Korean characters (expressed in Unicode) were displayed with broken encoding. 😅
The preliminary round problem was about writing VM escape shellcode for QEMU semihosting.
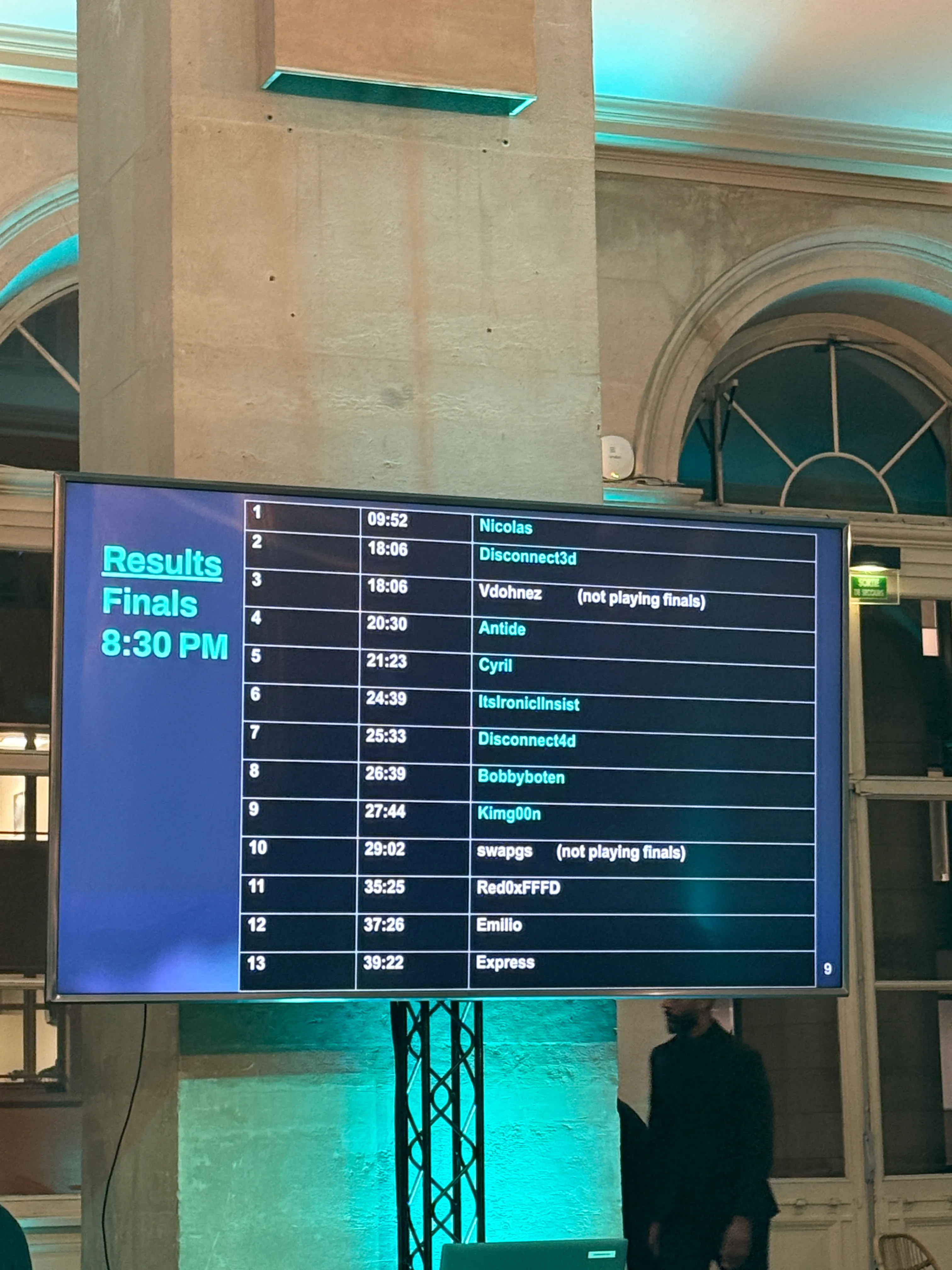 Actually, I thought I wouldn’t pass the preliminary round because the translation didn’t work and it took a long time to read the documentation.
I solved the problem in about 27 minutes, and the person who ranked higher than me suprisingly decided not to go to the finals, so I advanced to the finals.
Actually, I thought I wouldn’t pass the preliminary round because the translation didn’t work and it took a long time to read the documentation.
I solved the problem in about 27 minutes, and the person who ranked higher than me suprisingly decided not to go to the finals, so I advanced to the finals.
But I was eliminated right in the finals. 🥲
 Actually, I didn’t expect so many people to watch the finals.
The problem was a really easy shell coding problem, but my brain just shut down by the sound of people’s cheers. LOL
I tried to solve the problem without even looking at the IDA pseudocode properly.
Actually, I didn’t expect so many people to watch the finals.
The problem was a really easy shell coding problem, but my brain just shut down by the sound of people’s cheers. LOL
I tried to solve the problem without even looking at the IDA pseudocode properly.
Finals photo that i appeared in was taken by organizer and uploaded to hexacon’s x account.
If I participate next time, I’ll come back with even better skills. Actually, I was so embarrassed that everyone saw my screen. 😂 It felt like my coding skills were on display to the world…
But even though I lost in the finals, I was grateful for the champagne I received as a reward. 🍾
After not really enjoying the networking party on the first day, and watching the finals a little more, I went back to my accommodations and that was the end of the first day. Actually, my coworker was so tired that he went back to his room first, and my English speaking skills are like those of a 7-year-old, so I was a little afraid to talk to people. 😭
Second Day
On the second day, we went to the venue around 10 am, enjoyed a short coffee break, and continued listening to the presentation.
On the second day, there was a Korean presenter! Han-seo Kim gave a presentation on VirtualBox Escape, and it was impressive.

After the presentations on the second day, I attended a networking party held at a different pub-like venue.
The food was excellent, and the beer was delicious. It was great to chat with the Koreans I met at the conference.
I also had a lot of conversations with pumpkin, who is a researcher at DevCore, and researchers in Singapore. It was a truly enjoyable time, and I think it left unforgettable memories. I hope we can all meet again next time!
Conclusion
My English skills are lacking, so I’m deeply disappointed that I haven’t been able to talk to many people.
I’ll use this opportunity as a springboard to diligently study English.
Also, while listening to presentations on various topics, I had a thought: I want to diligently research vulnerabilities and create the opportunity to stand in that position someday.
My trip to Paris was enjoyable, and my participation in HexaCon 2025 was a valuable and unforgettable experience. I will definitely try harder to attend by speaker next time.
I would also like to thank my company, Raon Secure, and my Core Research Team(specialy to Team leader) for helping me achieve this experience.